*** Proof of Product ***
Exploring the Essential Features of “Mohamed Atef – CompTIA CSA+ – Certified Cyber Security Analyst”
CompTIA CSA+ / Certified Cyber Security Analyst
Get CompTIA CSA+ Certified easily
The CompTIA Cybersecurity Analyst, or CSA+, is a CompTIA certification focusing on the knowledge and skills required to configure and use threat-detection tools, perform data analysis, and interpreting the results with the end goal of securing an organization’
Cyber Security Consultant / Certified Instructor with more than 20 years of experience implementing and managing Cyber Security project such as:
- ISMS Implementation
- CS Standards / Compliance
- Security Operation Center
- BCP/DRP
- Penetration Testing
- CS Enterprise Technical Solutions
3 Books published
14 best sellers online courses
Professional Experience
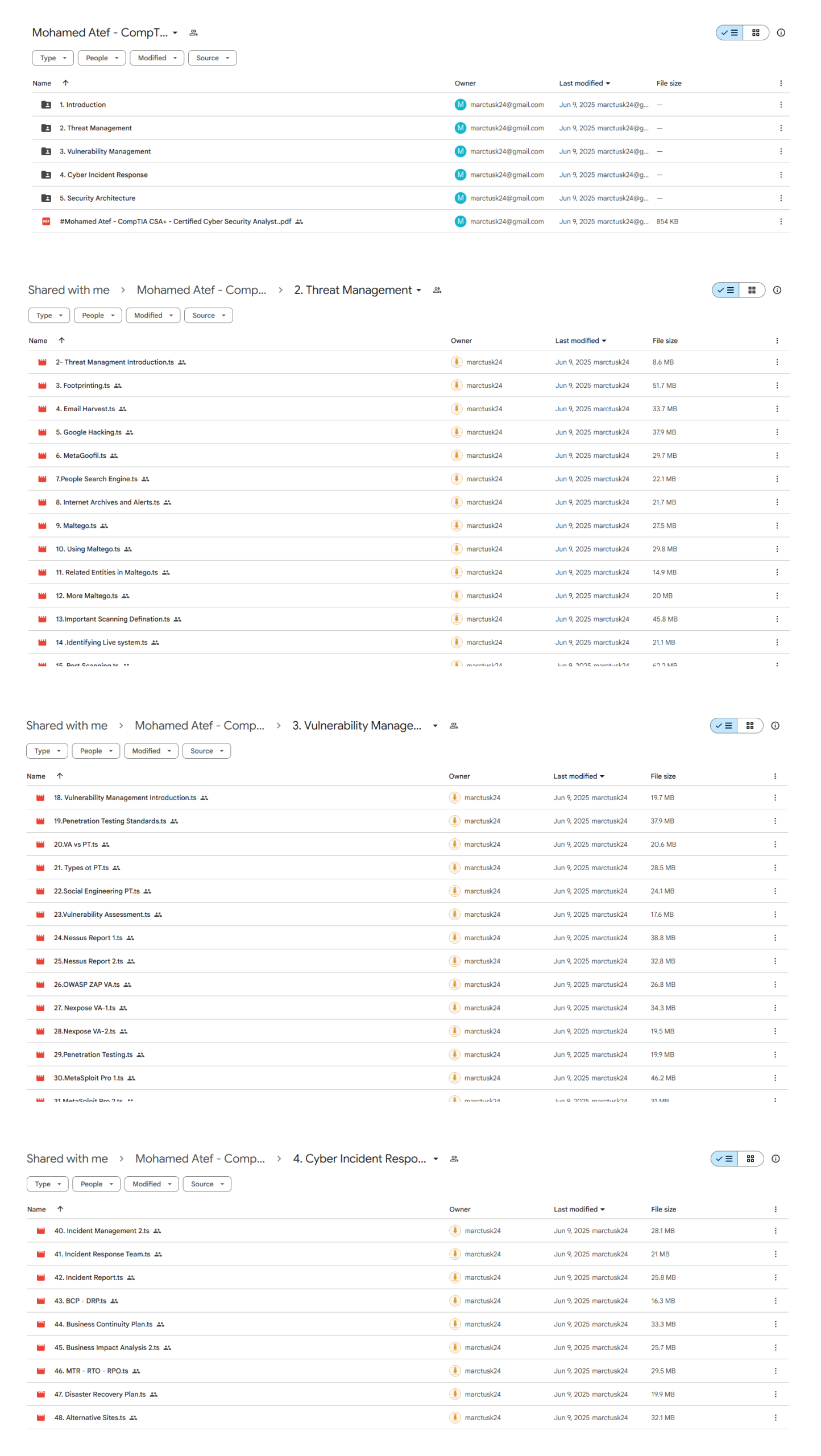
Course Curriculum
Introduction
- 1. Introduction (3:17)
Threat Management
- 2- Threat Managment Introduction (3:18)
- 3. Footprinting (14:12)
- 4. Email Harvest (9:51)
- 5. Google Hacking (10:36)
- 6. MetaGoofil (10:18)
- 7.People Search Engine (6:13)
- 8. Internet Archives and Alerts (7:04)
- 9. Maltego (8:40)
- 10. Using Maltego (8:14)
- 11. Related Entities in Maltego (3:51)
- 12. More Maltego (6:05)
- 13.Important Scanning Defination (13:19)
- 14 .Identifying Live system (6:41)
- 15. Port Scanning (14:24)
- 16.Advamced Scanning Techniques (7:23)
- 17.Network Mapping (11:41)
Vulnerability Management
- 18. Vulnerability Management Introduction (11:29)
- 19.Penetration Testing Standards (11:29)
- 20.VA vs PT (11:29)
- 21. Types ot PT (11:29)
- 22.Social Engineering PT (11:29)
- 23.Vulnerability Assessment (11:29)
- 24.Nessus Report 1 (13:25)
- 25.Nessus Report 2 (11:29)
- 26.OWASP ZAP VA (11:29)
- 27. Nexpose VA-1 (11:29)
- 28.Nexpose VA-2 (11:29)
- 29.Penetration Testing (11:29)
- 30.MetaSploit Pro 1 (14:32)
- 31.MetaSploit Pro 2 (11:29)
- 32.MetaSploit Pro 3 (11:29)
- 33.MetaSploit Community (11:29)
- 34.Armitage (11:20)
- 35.SQL Injection Introduction (11:20)
- 36. What is SQL Injection (11:20)
- 37.Is The Site Infected with SQL Injection (11:20)
- 38.The Amazing SQLMAP (11:20)
- 39.Live Example (11:20)
Cyber Incident Response
- 40. Incident Management 2 (11:25)
- 41. Incident Response Team (11:25)
- 42. Incident Report (11:25)
- 43. BCP – DRP (11:25)
- 44. Business Continuity Plan (14:36)
- 45. Business Impact Analysis 2 (11:25)
- 46. MTR – RTO – RPO (11:44)
- 47. Disaster Recovery Plan (11:25)
- 48. Alternative Sites (11:25)
Security Architecture
- 49. Common Security Architecture Frameworks (12:17)
- 50. Trusted Computing Base (11:16)
- 51. Security Models (17:08)
- 52. TCSEC (11:16)
- 53. ITSEC (11:16)
Please see the full list of alternative group-buy courses available here: https://lunacourse.com/shop/










 Media Buying ADS Masterclass - Mr Paid Ads
Media Buying ADS Masterclass - Mr Paid Ads  Just One Thing - John Mauldin
Just One Thing - John Mauldin  Henrique Barone - Classical Animation Workflow & Techniques
Henrique Barone - Classical Animation Workflow & Techniques  Deborah King - Spirit Guidance & Sacred Sutras - The Shift Network
Deborah King - Spirit Guidance & Sacred Sutras - The Shift Network  2-Day Psychopharmacology Course for Mental Health Clinicians - Susan Marie - PESI
2-Day Psychopharmacology Course for Mental Health Clinicians - Susan Marie - PESI  Stan Campbell - The Art of De-Escalation
Stan Campbell - The Art of De-Escalation  RSD Valentino- Hello To Never Leave Me – Invisible Game Decoded Full Manifesto
RSD Valentino- Hello To Never Leave Me – Invisible Game Decoded Full Manifesto  Alison Armstrong - Understanding Sex, Intimacy, Love & Commitment
Alison Armstrong - Understanding Sex, Intimacy, Love & Commitment  Fred Haug - Virtual Wholesaling Simplified
Fred Haug - Virtual Wholesaling Simplified  Gary Knight - Confronting Choice in Your Photojournalism Career
Gary Knight - Confronting Choice in Your Photojournalism Career  David Hans-Barker - Spiritual Hustlers Club
David Hans-Barker - Spiritual Hustlers Club  Chris Bale - Simplistic Seduction Video Course
Chris Bale - Simplistic Seduction Video Course  Taylor Welch and Chris - DIY ClientKit Fast-Track 2021
Taylor Welch and Chris - DIY ClientKit Fast-Track 2021  Nancy Cartwright - Teaches Voice Acting -MasterClass
Nancy Cartwright - Teaches Voice Acting -MasterClass  No Investment Guide: How to Get More Customers for Your PPC Agency
No Investment Guide: How to Get More Customers for Your PPC Agency  Team NFT Money - Ultimate NFT Playbook
Team NFT Money - Ultimate NFT Playbook  Roxanna Erickson-Klein - BT12 Conversation Hour 12 - The Home Life of Milton Erickson
Roxanna Erickson-Klein - BT12 Conversation Hour 12 - The Home Life of Milton Erickson  Jim Cockrum - Selling On Amazon Mentorship Series
Jim Cockrum - Selling On Amazon Mentorship Series  Alex Gould - CPA Wealth Academy Full Access
Alex Gould - CPA Wealth Academy Full Access  James Renouf & Max Gerstenmeyer - AI Influencer
James Renouf & Max Gerstenmeyer - AI Influencer  Candlecharts - Candlesticks MegaPackage Vol 1-4 (CCA)
Candlecharts - Candlesticks MegaPackage Vol 1-4 (CCA)  Influencer Video Secrets - Michelle Cunningham
Influencer Video Secrets - Michelle Cunningham  Greg Loehr - Advanced Option Trading With Broken Wing Butterflies
Greg Loehr - Advanced Option Trading With Broken Wing Butterflies  Oliver Velez - Essential Strategy Of Trade For Life
Oliver Velez - Essential Strategy Of Trade For Life  Steve Andreas - BT08 Workshop 07 - Disentangling and Clarifying Difficult Relationships
Steve Andreas - BT08 Workshop 07 - Disentangling and Clarifying Difficult Relationships  Ron Louis & David Copeland - How to Talk to Women
Ron Louis & David Copeland - How to Talk to Women  Sovereign Man Confidential - Renunciation Video
Sovereign Man Confidential - Renunciation Video  Ed Ponsi - Forex Trading
Ed Ponsi - Forex Trading  Dr Gabor Maté & Hameed Ali (A H Almaas) - Trauma + Awakening
Dr Gabor Maté & Hameed Ali (A H Almaas) - Trauma + Awakening  Emanuele Bonanni - My Trading Way
Emanuele Bonanni - My Trading Way  How to Build Strong Relationships at Work - Daniel Post Senning
How to Build Strong Relationships at Work - Daniel Post Senning  Dave Landry - Stock Selection Course
Dave Landry - Stock Selection Course  Forexmentor - Recurring Forex Patterns
Forexmentor - Recurring Forex Patterns  Pat Love - BT06 Workshop 36 - How to Improve a Relationship Without Talking
Pat Love - BT06 Workshop 36 - How to Improve a Relationship Without Talking  Carl Seidman - Demystifying The Role of an FP&A Professional
Carl Seidman - Demystifying The Role of an FP&A Professional  Charles Jayne - The Best of Charles Jayne
Charles Jayne - The Best of Charles Jayne  Kelly Counts - When Resuscitation Will Not Change the Outcomes: The Difficult Conversations
Kelly Counts - When Resuscitation Will Not Change the Outcomes: The Difficult Conversations  LJ Johnson - Beyond Certification: The Ultimate Travel Agent Education
LJ Johnson - Beyond Certification: The Ultimate Travel Agent Education  Atlas API Training - API 570 Exam Prep Training Course
Atlas API Training - API 570 Exam Prep Training Course  CPA Ads Academy & Mc Declan’s Bonuses - Brian Gonzalez, Stefan Ciancio & Timothy Miranda
CPA Ads Academy & Mc Declan’s Bonuses - Brian Gonzalez, Stefan Ciancio & Timothy Miranda  Sean Ellis - Growth Master Training Course
Sean Ellis - Growth Master Training Course  Raquel Spencer - Awakening the Multiverse Emerald Crystalline Energies
Raquel Spencer - Awakening the Multiverse Emerald Crystalline Energies  George Fontanills & Tom Gentile - Optionetics 6 DVD Series Home Study Course (Digital Download)
George Fontanills & Tom Gentile - Optionetics 6 DVD Series Home Study Course (Digital Download)  Susan Johnson & Daniel Hughes - Creating Healthy Attachment A Step-by-Step Guide to Apply Proven Models in Everyday Therapy
Susan Johnson & Daniel Hughes - Creating Healthy Attachment A Step-by-Step Guide to Apply Proven Models in Everyday Therapy  Arnold Haultain - Hints for Lovers
Arnold Haultain - Hints for Lovers  Paul Janka - Seduction Materials Collection ( DeluxeBundle)
Paul Janka - Seduction Materials Collection ( DeluxeBundle)  Martha Teater - Treating Chronic Pain: Proven Behavioral Tools - PESI
Martha Teater - Treating Chronic Pain: Proven Behavioral Tools - PESI  Steven Capobianco & Mitch Hauschildt - RockTape Functional Movement Techniques Certification: Kinesiology Taping Interventions & More
Steven Capobianco & Mitch Hauschildt - RockTape Functional Movement Techniques Certification: Kinesiology Taping Interventions & More  Bruno Bettelheim, Albert Ellis, Ronald Laing & Judd Marmor - EP85 Panel 16 - Sexuality
Bruno Bettelheim, Albert Ellis, Ronald Laing & Judd Marmor - EP85 Panel 16 - Sexuality  Jared Platt - The Ultimate Lightroom Classic CC Workflow
Jared Platt - The Ultimate Lightroom Classic CC Workflow  Jesse Livermore Trading System - Joe Marwood
Jesse Livermore Trading System - Joe Marwood  Duston McGroarty - 1st Page Academy
Duston McGroarty - 1st Page Academy  Albert Dros - Full Editing Course on Landscape Photography
Albert Dros - Full Editing Course on Landscape Photography  Crypto Dan - The Crypto Investing Blueprint To Financial Freedom By 2025
Crypto Dan - The Crypto Investing Blueprint To Financial Freedom By 2025  Elizabeth (Liz) Campbell - Update Your Infusion Therapy Toolbox - PESI
Elizabeth (Liz) Campbell - Update Your Infusion Therapy Toolbox - PESI  Merideth Norris, Kinna Thakarar, Michael Wardrop - 2020 Maine Opioid Crisis Bundle
Merideth Norris, Kinna Thakarar, Michael Wardrop - 2020 Maine Opioid Crisis Bundle  Ron LeGrand - Wholesale Retail Bootcamp
Ron LeGrand - Wholesale Retail Bootcamp  Paul Rhines - Eye Accessing Cue Mastery
Paul Rhines - Eye Accessing Cue Mastery  Taoist Breathing 2022 Summer Retreat (Two Weeks) - Bruce Frantzis
Taoist Breathing 2022 Summer Retreat (Two Weeks) - Bruce Frantzis  SMB - Options Training
SMB - Options Training  Code Star Academy, Oracle Master Training - SQL for Beginners: The Easiest Way to Learn SQL Step by Step
Code Star Academy, Oracle Master Training - SQL for Beginners: The Easiest Way to Learn SQL Step by Step  The Thyroid Body Type Course - Eric Berg
The Thyroid Body Type Course - Eric Berg  Steven Kotler - Lost Content
Steven Kotler - Lost Content  Adam Armstrong - 37 Secrets About Women And Sex
Adam Armstrong - 37 Secrets About Women And Sex  Visti Larsen - Pisces: learn the importance of the Guru, mantra and remedies for life
Visti Larsen - Pisces: learn the importance of the Guru, mantra and remedies for life  Kelly Pickens Pickens - Adult ADHD Medications & The Recent Increase in Prevalence
Kelly Pickens Pickens - Adult ADHD Medications & The Recent Increase in Prevalence  Simpler Trading - Bruce Marshall - The Options Defense Course
Simpler Trading - Bruce Marshall - The Options Defense Course  Marisa Murgatroyd - Call To Adventure
Marisa Murgatroyd - Call To Adventure  Money Miracle - George Angell - Use Other Peoples Money To Make You Rich
Money Miracle - George Angell - Use Other Peoples Money To Make You Rich